- Home
- About
- Industries Served
- Capabilities
- Digital Transormation
- Business Transformation
- Cyber Security
- Sustainability Strategy Advisory
- ESG Disclosures
- Net Zero Carbon
- Article 6 and Carbon Pricing
- Low Carbon Solutions
- Climate Reduction Regulatory Compliance
- Nationally Determined Contributions
- Contract Catalyst
- Accreditation Advisory
- Management System
- People Strategy
- GRC
- Case Studies
- Resources
- News
- Contact
Cyber Security
- Home
- Cyber Security
Cyber Security
CYBERCRIME AND ISO 27001
As digitalization increases, so do people’s chances of being affected by online crime. Nearly nine out of 10 web app attacks use stolen data, and 18% of common items for sale on the dark web are passwords, emails and account data, NordPass says.Overall, 24 billion different online credentials – such as usernames and passwords – have been stolen since 2016. That’s roughly three for every person on the planet.
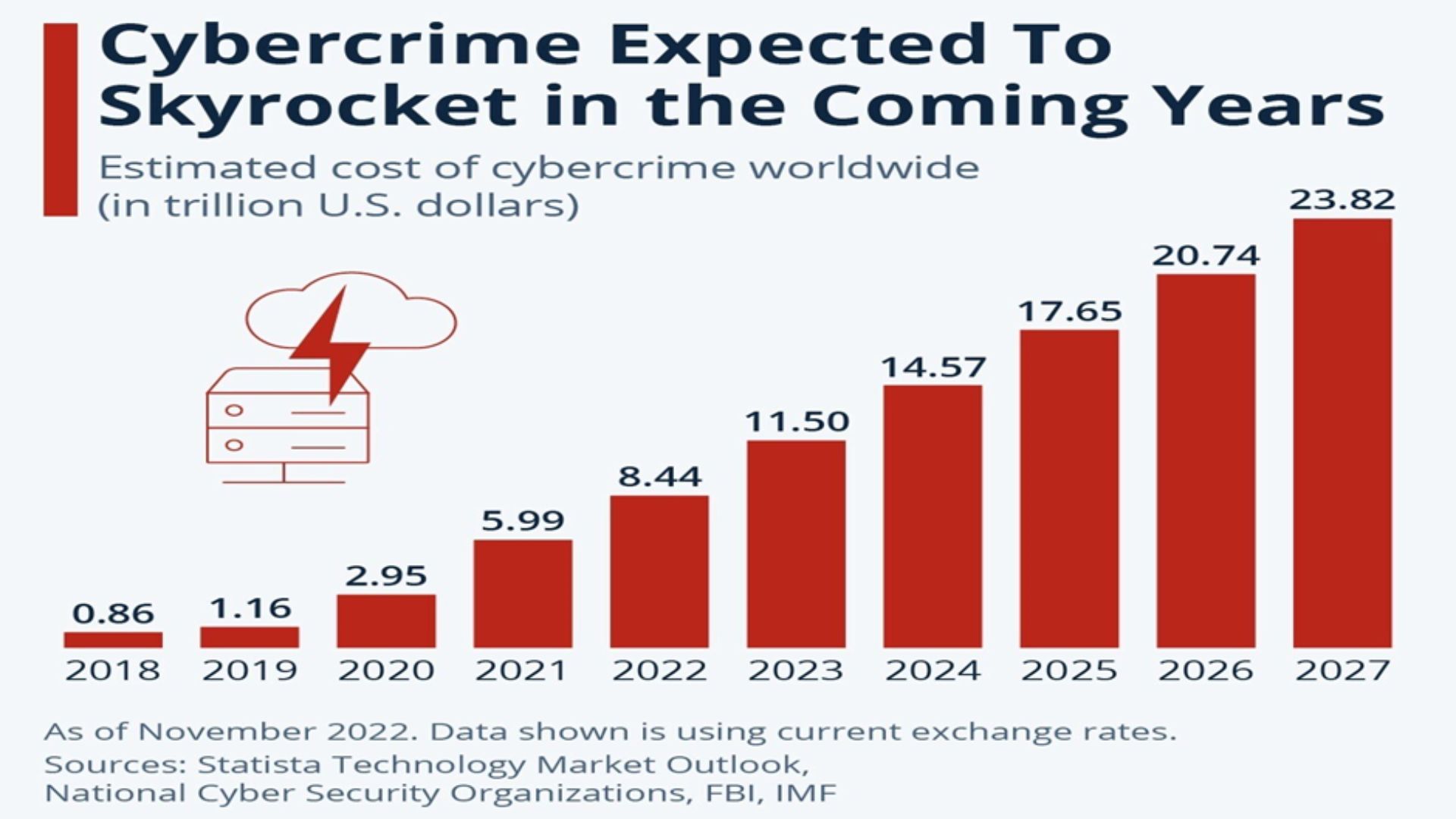
All this means the cost of cybercrime is soaring, and is expected to exceed $17.65 trillion in 2025.Organizations that have not adopted or implemented a cyber security framework are the most vulnerable to cyber-crime, including successful phishing attacks, ransomware, or data theft, among others. A cyber security framework is essential for protecting sensitive data, including regulating access to critical information systems and networks.
The information security management system (ISMS) described in ISO/IEC 27001 is one of the world’s best-known and most trusted cyber security frameworks. It is a consensus-based international standard based on industry best practices.
The cost of not having an ISMS or other effective security measures in place can be detrimental to any business, not only financially but also in terms of reputational damage. Litigation poses a serious threat to organizations, especially in cases where customers, employees, or business partners suffer actual financial losses.
And that is not restricted to cases where hackers steal credit card data, for example. The phrase “actual financial losses” could also refer to a drop in a company’s share price.
3.1 Cybersecurity & Digital Risk (ISO 27001)
Overview
Cybersecurity is an ever-evolving challenge, and businesses must adopt comprehensive frameworks to safeguard sensitive data and mitigate risks. SSTC specializes in implementing ISO 27001, a globally recognized standard for Information Security Management Systems (ISMS). With a focus on proactive risk management and regulatory compliance, we help organizations secure their digital assets, ensuring data protection and resilience against evolving cyber threats.
Our Approach
ISO 27001 Implementation
We guide you through the process of implementing ISO 27001 by assessing current security practices and establishing an ISMS that aligns with the ISO 27001 standard. This includes risk assessments, defining security controls, and implementing necessary safeguards.
Cyber Risk Management
SSTC helps identify, assess, and manage cyber risks by employing advanced threat detection, monitoring, and response systems. Our cybersecurity framework ensures that risks are continuously mitigated, protecting critical business operations.
Continuous Improvement & Monitoring
Cybersecurity is a moving target. SSTC ensures continuous monitoring of your security infrastructure, making real-time adjustments to stay ahead of emerging threats.
Employee Training & Awareness
We prioritize employee training, ensuring staff understands best practices for cybersecurity, reducing internal vulnerabilities and improving organizational security posture.
Impact to Customers
➺ Risk Mitigation: Reduced risk exposure and minimized vulnerabilities through a structured ISMS.
➺ Regulatory Compliance: Achieve and maintain compliance with ISO 27001, enhancing business credibility and trust.
➺ Operational Resilience: Continuous protection of your digital infrastructure against evolving cyber threats.
3.2 Cyber Security Vendor Management
Overview
This service focuses on managing and securing your vendor relationships by ensuring that third-party providers adhere to robust cybersecurity standards. We assess potential vulnerabilities introduced by external partners and take proactive steps to mitigate risks throughout the software supply chain.
Our Approach
Secure Coding Practices
Implement foundational security principles into the development lifecycle to ensure that vendors' software is resilient against potential threats. This includes setting guidelines for using trusted open-source components and ensuring that vendor developers follow secure coding standards.
Software Bill of Materials (SBOM
Work with vendors to implement SBOMs, providing a comprehensive list of all components used in their software. This enhances transparency in the software supply chain, allowing your organization to identify potential security risks associated with third-party components.
Continuous Monitoring
Set up AI-powered tools to proactively monitor vendor software and systems for vulnerabilities. This helps detect threats early and ensures that vendor software is regularly updated to stay ahead of security risks.
Vendor Security Updates
Regularly assess vendor cybersecurity practices and policies to identify gaps and vulnerabilities. Provide recommendations to strengthen security measures and ensure that vendors stay updated in line with the latest cybersecurity best practices.
Impacts
➺ Reduced Vendor-Related Risks: By ensuring vendors follow secure coding practices and SBOM guidelines, we significantly reduce the likelihood of vulnerabilities introduced by third-party providers.
➺ Enhanced Supply Chain Security: Continuous monitoring and regular vendor security updates strengthen your organization’s defense against external threats, reducing the risk of supply chain attacks.
➺ Improved Vendor Transparency: The implementation of SBOMs ensures full visibility of third-party software components, allowing for more informed risk management decisions.
